Hackers inject malware in servers around the globe
August 3, 2012Hackers are selling malware online which can be use to attack a vulnerability on popular webserver administrative tool Parallels Plesk Panel.
Brian Krebs, respected ex-Washington Post journalist and security blogger of krebsonsecurity.com, has stated that “Hackers in the criminal underground are selling an exploit that extracts the master password needed to control Parallels’ Plesk Panel”.
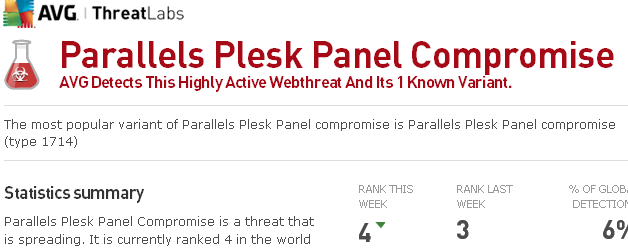
The malware is spreading rapidly and is currently ranked 4 in the world for online threats. With a noticeable spike in detection 0n July 18, Parallels Plesk Panel Compromise was detected on servers in 153 countries in July. AVG reports that there are currently 6,331 websites in 34 countries which host the malware.
On ZDNet, Michael Lee raise the question whether this is the result of hacker capitalising on an earlier Exploit (repaired in February) or if this ” Zero Day” Exploit is a new development.
If your website displays an alert or the malware is detected on your server, ask your IT support team to immediately replace the infected javascript files and install the Plesk vulnerabilty patch.
Parallels Plesk product information
IMPACTED PLESK VERSIONS
Parallels Plesk Panel 9.5x and 10 include this vulnerability (no prior versions have that component). Parallels Small Business Panel 10.2 is also affected.
OVERVIEW OF THE VULNERABILITY AND EXPLOIT
A flaw in the popular ProFTPD FTP server potentially allows unauthenticated attackers to compromise a server. The problem is caused by a buffer overflow in the pr_netio_telnet_gets() function for evaluating TELNET IAC sequences.
ProFTPD bug report: http://bugs.proftpd.org/show_bug.cgi?id=3521
DETAILS ON THE VULNERABILITY AND EXPLOIT
ProFTPD is capable of processing TELNET IAC sequences on port 21; the sequences enable or disable certain options not supported by the Telnet or FTP protocol itself. The buffer overflow allows attackers to write arbitrary code to the application’s stack and launch it. Updating to version 1.3.3c of ProFTPD solves the problem. The update also fixes a directory traversal vulnerability which can only be exploited if the “mod_site_misc” module is loaded. This flaw could allow attackers with write privileges to leave their permitted path and delete directories or create symbolic links outside of the path. The module is not loaded or compiled by default.
Sources:
http://www.parallels.com/au/products/plesk/ProFTPD/
http://www.avgthreatlabs.com/webthreats/info/parallels-plesk-panel-compromise/
http://www.zdnet.com/hackers-leverage-plesk-panel-to-attack-websites-7000000651/
http://krebsonsecurity.com/2012/07/plesk-0day-for-sale-as-thousands-of-sites-hacked/
From Our Clients


Digital Tsunami was professional, responsive and accurately interpreted our brief. The final result was a new website that was in keeping with the iBurst brand essence and proposition.


I'm very pleased with my new website. Clean, crisp and well-ordered. Many thanks to Andrew and the team at Digital Tsunami for their speedy work and dedicated follow up, ensuring a glitch-free launch!


The launch .. was a success. We were able to present this live on a Wireless connection during our Sydney, Australia sales conference on a location with very limited internet bandwidth. This proves the technology used .. renders light webpages which are easy to download on a browser.
Comments I've heard from our employees were all positive and reflected precisely what we were looking for: a simple but concise, clean and effective webpage.
We acknowledge the timeframe given to you was extremely short but nevertheless you have sucessfully delivered the project on schedule .. the critical success factor was communication and availability of Digital Tsunami's team.
I am very glad we were able to partner with such a professional team as yours and I am confident any other initiatives with you will be as successful.


Thank you for the development of an updated brand image for Wah Yuet in China.
While originally contracted to produce a video highlighting Wah Yuet's manufacturing capabilities, it was apparent very quickly that your understanding of our requirements, combined with your experience, were the perfect fit to create a new logo and style guidelines for the company. While relatively small in scope, you were dedicated to the success of the project and I am pleased to say that you hit the bullseye!


(We) took a fairly substantial audit of .. sophisticated sites both technically and creatively .. Out of six prominent designers, Digital Tsunami stood out.
The quality of the images, the sophisticated management of text .. together with smooth animations makes (our) website of very high calibre.
I would personally rate this site in the top 2 percent of world wide web sites today.