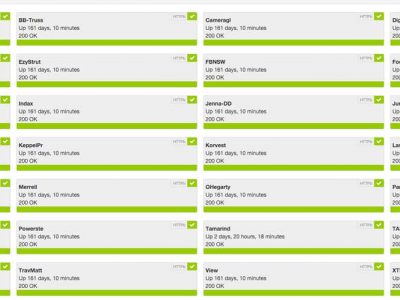
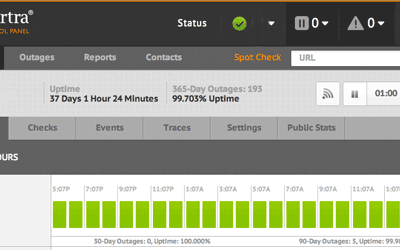
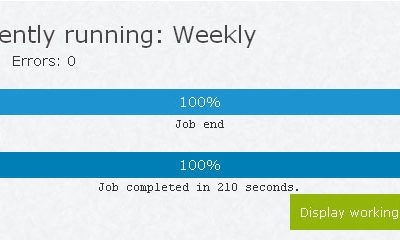
We all understand the critical importance of maintaining an online presence. The image above displays a live uptime report relating to sites hosted by Digital Tsunami. On private clouds and dedicated web servers in the USA, China, Hong Kong and Australia, Digital Tsunami has been hosting websites since, well .. last century! Over the last quarter, uptime has been 99.988% …Read More…