Shellshock – Bash Vulnerability
September 24, 2014Shellshock is a serious security vulnerability in Bourne-Again SHell (BASH) on Linux.
Known as the “Bash Bug” or “ShellShock”, the GNU Bash Remote Code Execution Vulnerability (CVE-2014-6271) could allow an attacker to gain control over a targeted computer if exploited successfully.
First disclosed on 24 September 2014, the vulnerability potentially affects most versions of Linux and Unix operating systems, in addition to Mac OS X (which is based around Unix).
Within an hour of the announcement of the Bash vulnerability, there were reports of machines being compromised by the bug. By 25 September 2014, botnets based on computers compromised with exploits based on the bug were being used by attackers for distributed denial-of-service (DDoS) attacks and vulnerability scanning.
On 26 September 2014, a Shellshock-related botnet was being used for a DDoS attack against Akamai Technologies and to scan the United States Department of Defense.
By 30 September, the website performance firm CloudFlare said it was tracking approximately 1.5 million attacks and probes per day related to the bug.
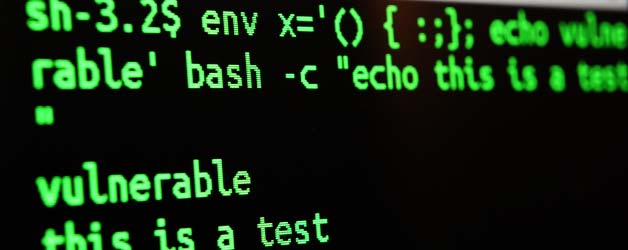
The vulnerability affects Bash, a common component known as a shell, that appears in many versions of Linux and Unix. Bash acts as a command language interpreter. In other words, it allows the user to type commands into a simple text-based window, which the operating system will then run.
Bash can also be used to run commands passed to it by applications and it is this feature that the vulnerability affects. One type of command that can be sent to Bash allows environment variables to be set.
According to RedHat, “An attacker could use this flaw to override or bypass environment restrictions to execute shell commands. Certain services and applications allow remote unauthenticated attackers to provide environment variables, allowing them to exploit this issue.”
Environment variables are dynamic, named values that affect the way processes are run on a computer. The vulnerability lies in the fact that an attacker can tack-on malicious code to the environment variable, which will run once the variable is received.
Read more items related to security.
Discovered on 12 September 2014, analysis of the source code history of Bash shows the vulnerabilities had existed since version 1.03 of Bash released in September 1989. The developers (and current maintainers) of BASH were immediately notified by the discoverer, in order to allow time to develop and test a security patch.
There was an original fix published for CVE-2014-6271, but within days, a second advisory was issued (CVE-2014-7169) to address further risks. Intense scrutiny of the underlying design flaws discovered a variety of related vulnerabilities, (CVE-2014-6277, CVE-2014-6278, CVE-2014-7169, CVE-2014-7186, and CVE-2014-7187); which maintainer Chet Ramey addressed with a series of further patches.
Some Digital Tsunami client sites are hosted on our own, or client-exclusive, private clouds on Linux-based platforms. These clouds had the potential to be exposed to this vulnerability.
However, within hours of the official announcement of the vulnerability, the security patch was applied to all Digital Tsunami Linux web servers. Sites hosted on the Windows platform are not subject to the vulnerability.
No Digital Tsunami clients on our private clouds were affected by the recent Heartbleed vulnerability.
Sites hosted on external servers will remain at risk until security patches are applied.
For enquiries on advanced security for your web presence, please contact Digital Tsunami Sales or Technical Support.
External References:
Oracle
Red Hat Security Advisory on CVE-2014-7169
Shellshocker
Symantec
Ubuntu Security FAQ
US Computer Emergency Readiness Team
From Our Clients


.. organised, meticulously detailed and yet flexible - always serving client needs to the highest standards. From a client perspective, you can expect high quality, timely completion and minimal fuss.


Andrew has provided Merrell Associates with reliable service, bringing a vast wealth of knowledge in IT to the task for more than the eight years I have been working here.
We have been helped by Andrew to solve all sorts of problems and if there isn't an immediate fix, solutions are found pretty quickly.


Andrew was able to create an entirely new website in a short period of time and to budget. He and his team worked very well with both our Marketing and IT team.


The services provided included the registration of our domain name, establishment of our email accounts, and development & hosting of our website, were all executed rapidly and effectively. We also appreciate the service of upgrading our list of 150 shelf company names (in Chinese characters and English) every 2 weeks.
We valued the high level of creative design provided by Digital Tsunami, both for the website and the corporate identity.


I have enjoyed working with you on this important project and have been particularly impressed by your company's professionalism. The speed and accuracy of your work has been first rate and your creative input has been instrumental to the success of the project.